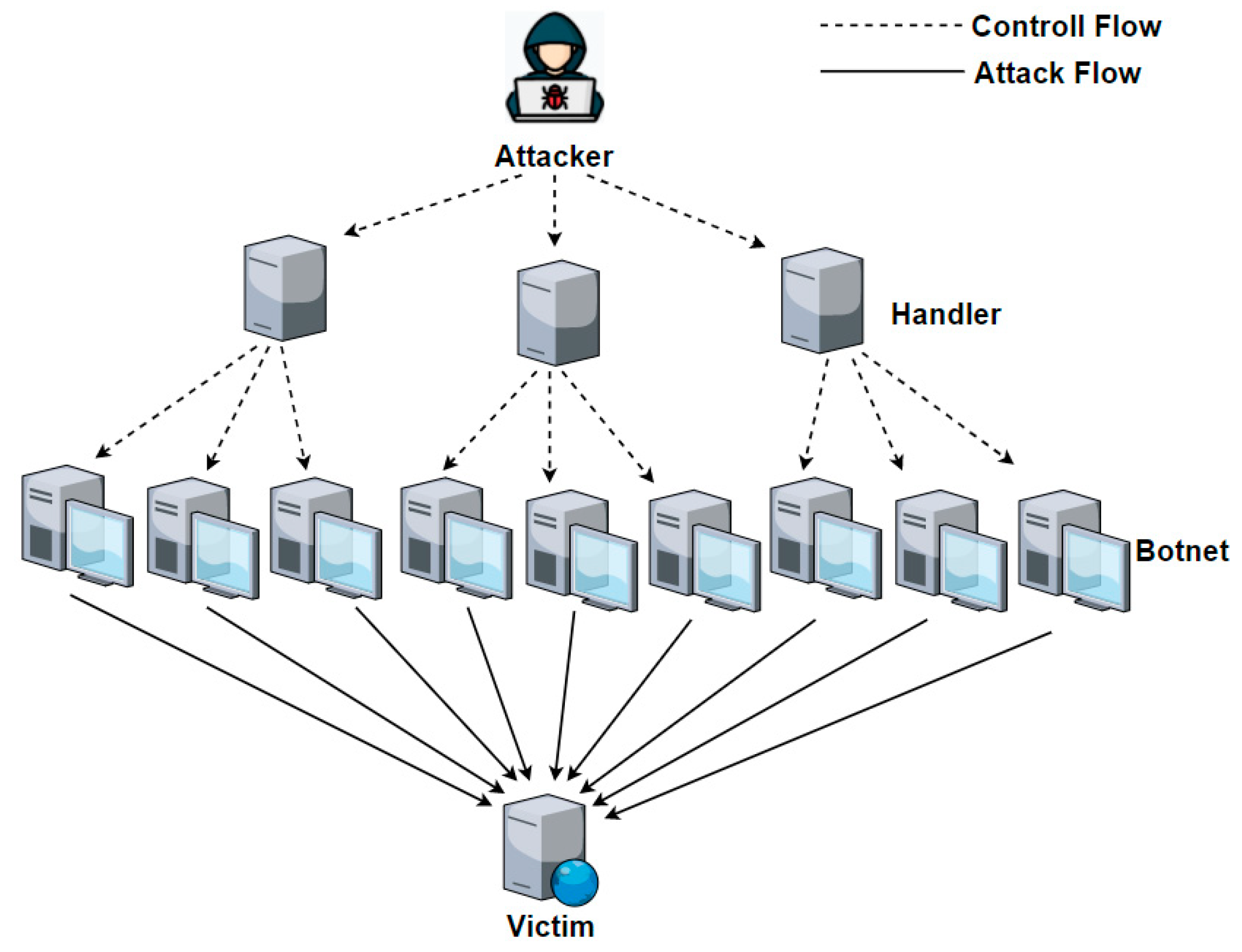
Applied Sciences | Free Full-Text | Detection of Unknown DDoS Attacks with Deep Learning and Gaussian Mixture Model
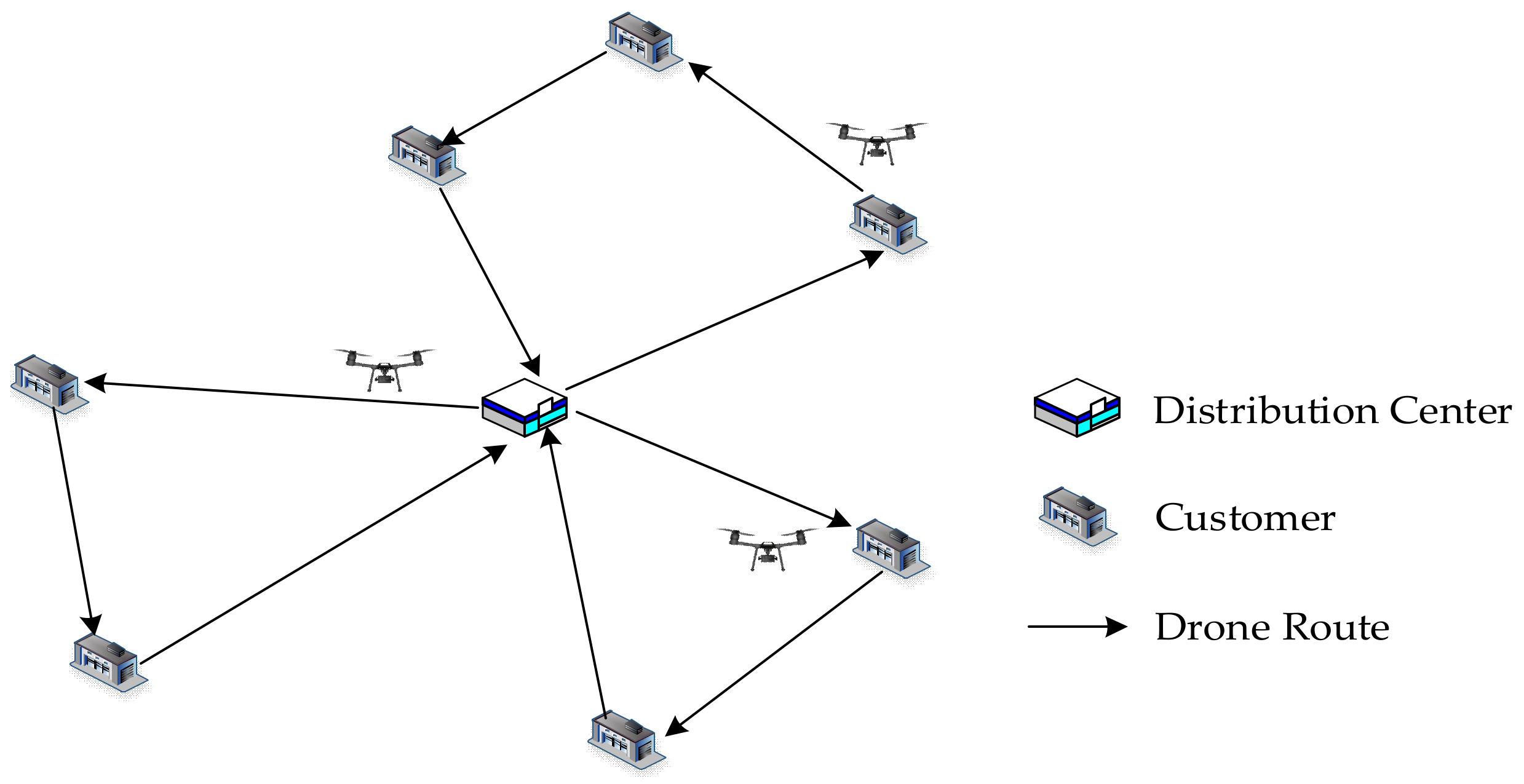
Sustainability | Free Full-Text | Optimal Model and Algorithm of Medical Materials Delivery Drone Routing Problem under Major Public Health Emergencies | HTML

Game theoretic solution for an Unmanned Aerial Vehicle network host under DDoS attack - ScienceDirect

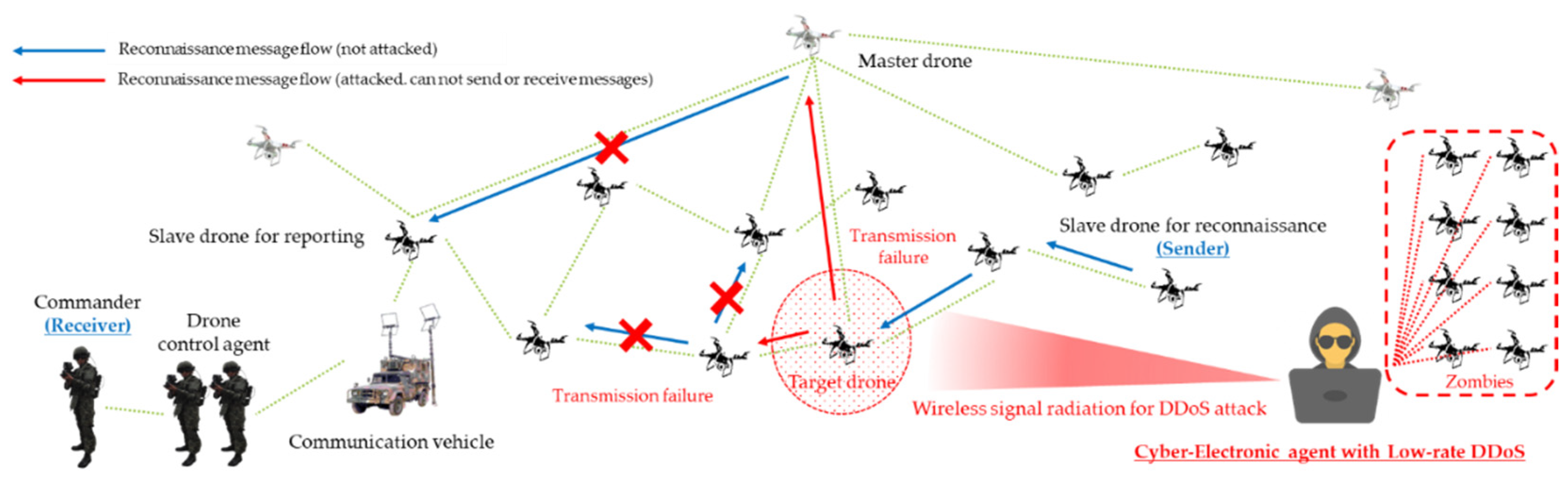
Sensors | Free Full-Text | D-CEWS: DEVS-Based Cyber-Electronic Warfare M&S Framework for Enhanced Communication Effectiveness Analysis in Battlefield | HTML

GitHub suffers from a DDoS attack, Amazon moves drones to Canada, IBM Watson acquires Blekko—SD Times news digest: March 30, 2015 - SD Times
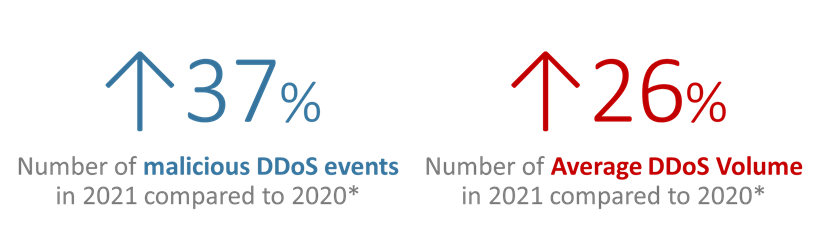
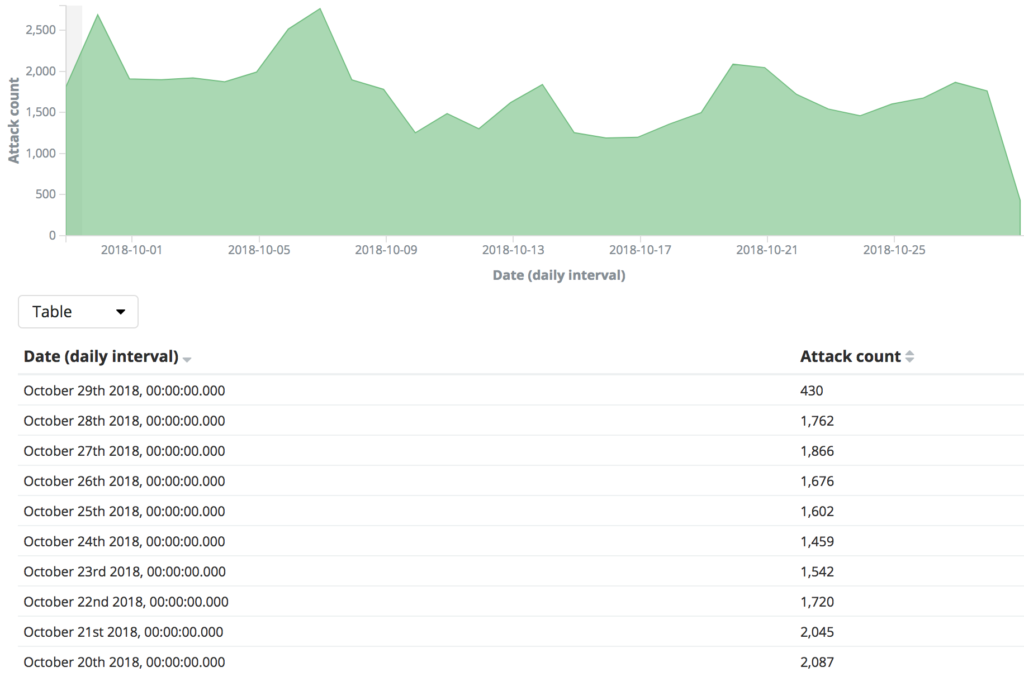
DDoS Protection in the Age of 5G Networks, Edge Computing and Explosive Bandwidth Growth - Security Boulevard
Securing Against DoS/DDoS Attacks in Internet of Flying Things using Experience-based Deep Learning Algorithm
Securing Against DoS/DDoS Attacks in Internet of Flying Things using Experience-based Deep Learning Algorithm

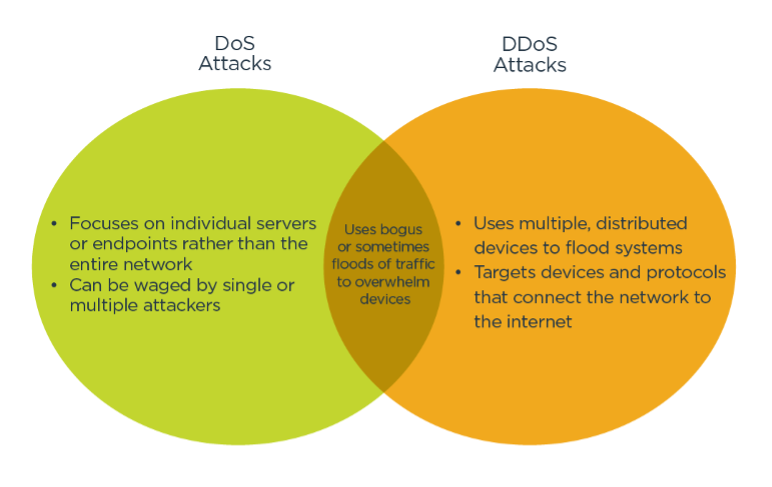
Concerns Security | Distributed Denial of Service Attacks | Moral Issues, Societal Factors Security Although distributed computing looks to provide an efficient means of conducting extraordinarily large scale computations, there are numerous privacy and ...
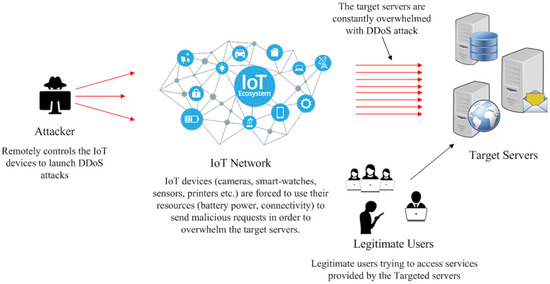
Sensors | Free Full-Text | Blockchain Based Solutions to Mitigate Distributed Denial of Service (DDoS) Attacks in the Internet of Things (IoT): A Survey
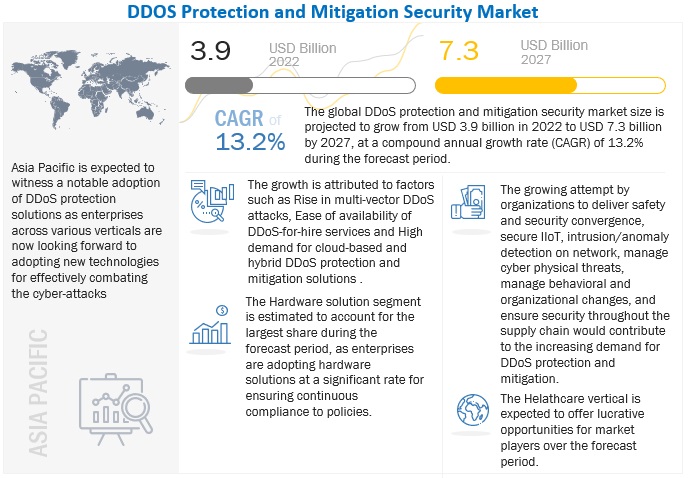
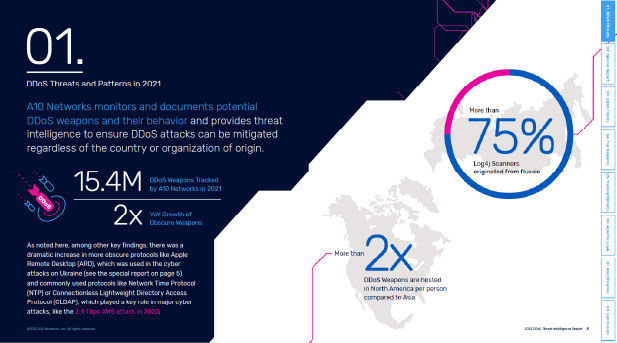
DDoS Protection and Mitigation Market Size, Share and Global Market Forecast to 2026 | MarketsandMarkets
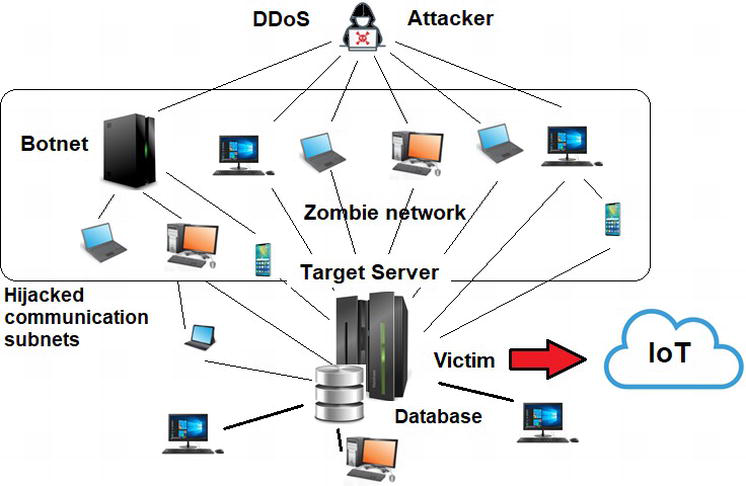
Internet of Things and Distributed Denial of Service as Risk Factors in Information Security | IntechOpen